As an administrator, you know that securing your Dynamics 365 data isn’t optional. With threats piling up faster than ever, a breach could wreck your organisation’s reputation.
This is why having a rock-solid security strategy is critical. You’ve got to protect your organisation from these ever-increasing risks, meet compliance standards without treating them like a checkbox exercise, and retain trust. This requires a well-thought-out approach to manage, secure, and maintain the integrity of your system.
This article shares five recommendations for strengthening security in Dynamics 365 CRM and Power Apps.
1. Review Role-Based Security Permissions
We recommend adopting the principle of least privilege (PoLP) for user security. This states that people should only have access to the specific applications and data needed to do their job.
Role-based security is essential for applying PoLP across teams and simplifying user management.
Custom security roles are always recommended to ensure they reflect your organisation’s unique security policy. By using custom roles, you can avoid potential issues if subsequent Microsoft updates automatically make changes to the standard security roles.
We recommend regularly reviewing security roles at least annually to ensure they are correctly aligned with your current business requirements. For instance, are all custom roles still needed? Do these permissions align with the PoLP? Did a specific privilege increase temporarily to allow certain access requirements that can now revert to the original setting?
2. Check Export Options
An integral part of a security role review should examine export permissions.
While these permissions support data analysis and reporting, inadequate management could turn them a source of data breaches.
Granting export permissions means that users can export data from any table or entity they can access, such as contacts and leads.
Additionally, consider the export of data from apps through reports, especially those initiated by SQL Server Reporting Services (SSRS), as these may also contain organisational information.
For a strong security posture, scrutinise export permissions closely. Restrict them based on necessity and unique role requirements, ensuring only those who genuinely need them are granted access.
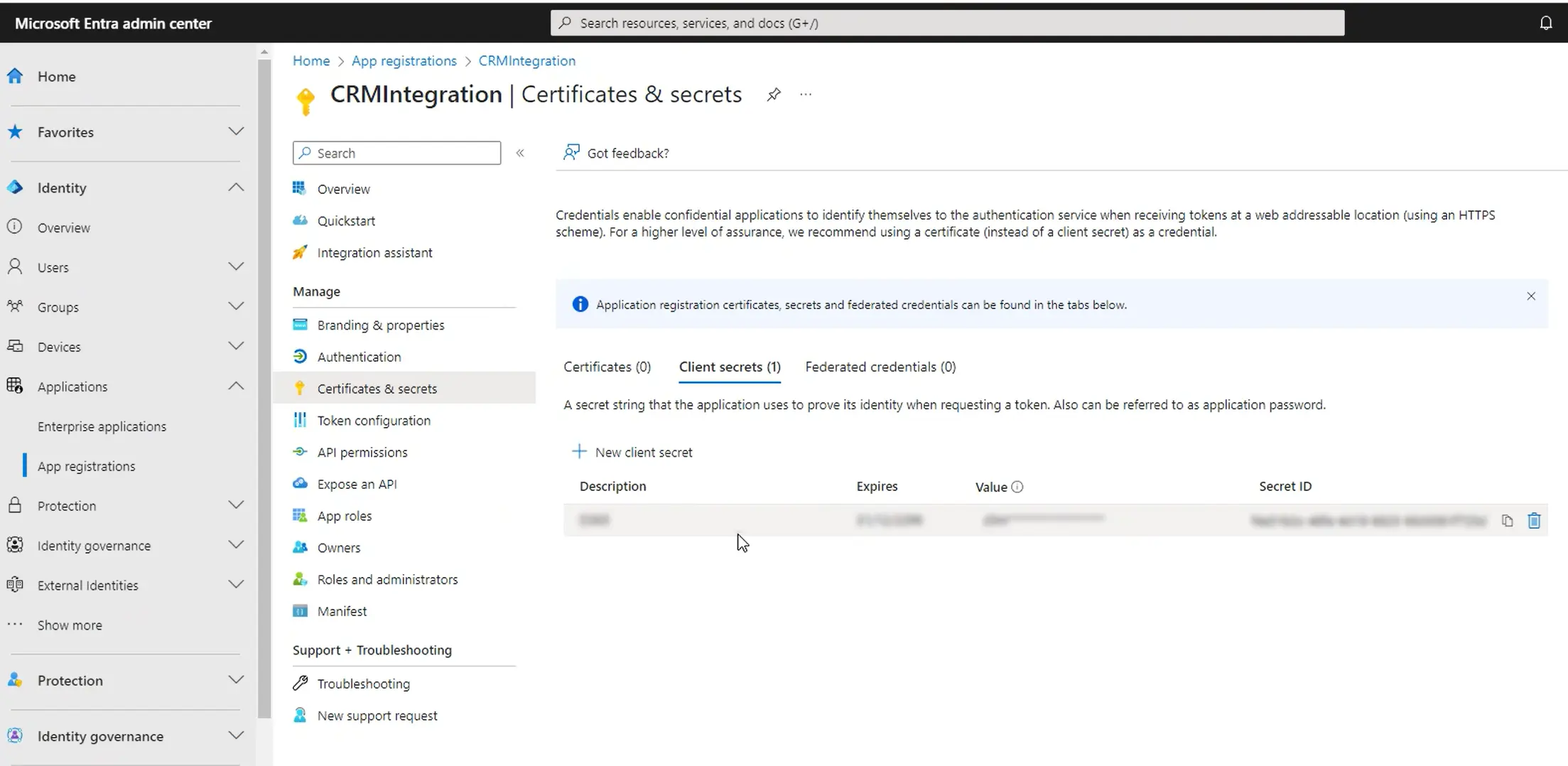
3. Client Secrets Expiry Settings
In Microsoft Entra (previously Azure Active Directory), credentials are used by confidential client applications that access a web API. These credentials enable Dynamics 365 and other apps to identify themselves to the authentication service upon receiving tokens at a web location.
Certificates are the recommended credential type as they’re considered the most secure, but client secrets are popular due to their ease of use.
What are client secrets?
These are essentially secret strings that serve as application passwords. Applications need a client secret to prove their identity when requesting a token. Client secrets play a vital role in authorising and authenticating applications and APIs in Azure.
Managing Client Secrets Expiry
If your organisation uses client secrets as its credential type for Dynamics 365, these expiry settings should be regularly reviewed.
We recommend administrators set an expiration value of less than 12 months to change their client secrets or update the secrets whenever key IT staff leave the business.
Regular alteration mitigates the risk of outdated strings falling into the wrong hands.
Learn more in our article, Best Practices for Managing Clients Secrets
4. Multifactor Authentication (MFA)
Implementing MFA bolsters security by providing an extra protection layer beyond passwords.
The MFA feature in Microsoft Entra requires people to authorise their identities using a second verification method in conjunction with their usual login credentials. This significantly enhances the defence mechanism of your cloud infrastructure for Dynamics 365 and Microsoft 365 apps.
Supplementary verification can be a uniquely generated code sent to an authenticator app on a person’s mobile device. This can curb unauthorised access because even if passwords suffer a compromise, MFA will continue to act as a gatekeeper.
Database administrators are strongly recommended to implement MFA as part of their security strategy. MFA within offers a seamless and efficient solution to secure your CRM data, ensuring your organisation’s information is well-protected and your operations continue non-disrupted.
5. Audit Logging
Another tool is the auditing feature that tracks user activity, system changes, and data access.
By activating audit trails, you generate a detailed log, meticulously tracking user activity, system changes, and data access within your environment. Should an incident arise, these logs provide a reliable resource for investigation, allowing administrators to pinpoint issues and take corrective action swiftly.
Audit trails also offer invaluable support for compliance. They provide a chronological record of data access and alterations, demonstrating due diligence and adherence to regulatory requirements.
Related: Is Your Audit Policy Aligned with Your Business Needs?
Final Thoughts
Prioritising data security in Dynamics 365 is fundamental for safeguarding your business data and meeting compliance requirements. Contact ServerSys for help to refine your security protocols and ensure the highest data protection standards.